Hack the Box rev DebugMe
Description
A develper is experiementing with different ways to protect their software. They have sent in a windows binary that is suposed to super secureand really hard to debug. Debug and see if you can find the flag.
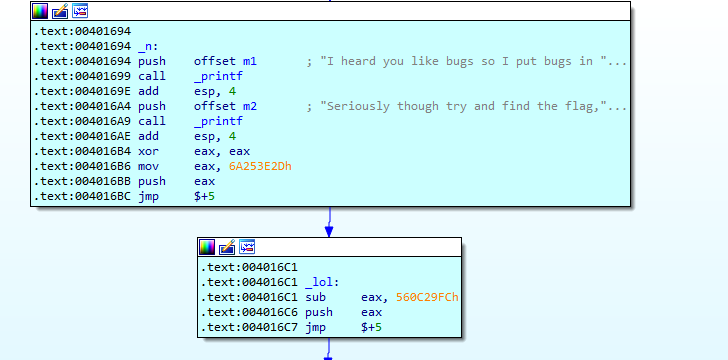
The executable is an anti-debug check with the flag being put on the stack at the end.
The first debug check is done by getting the PEB located at fs:30h and getting the ISdebugger bit from it. Normal would be 0 and I had 0x1
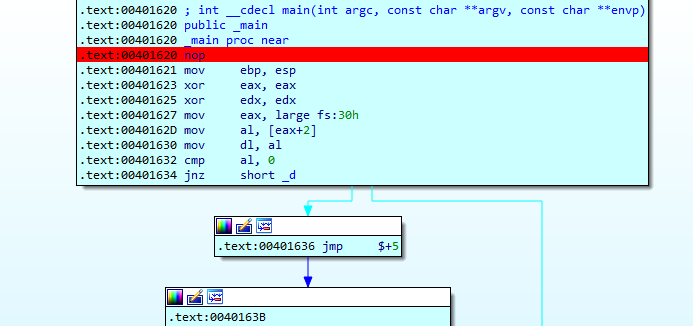
The second check is done by PEB.NtGlobalFlag (offset 0x68, normal 0x0), i had 0x70
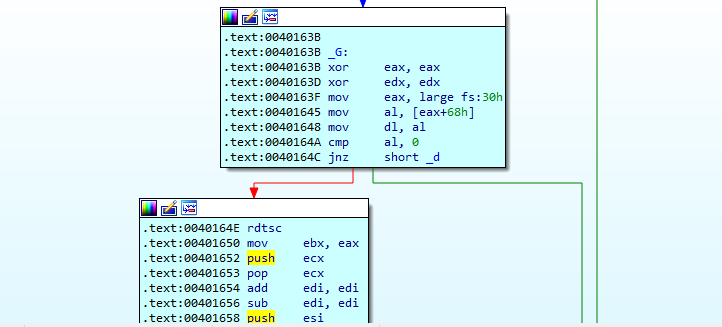
Further down the executable it will make and call main which will do the same checks.
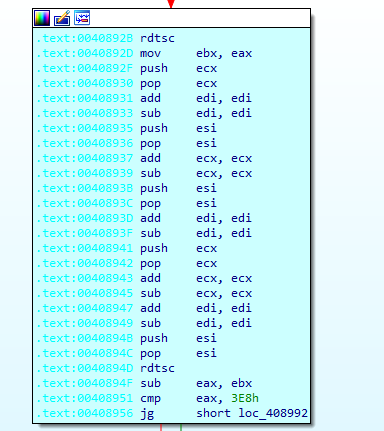
The last debug check is made by timing with 2 rdtsc instructions .
Afterwards the main function is built by xoring some memory. The main will contain the same checks seen here and afterwards the flag will be built on the stack
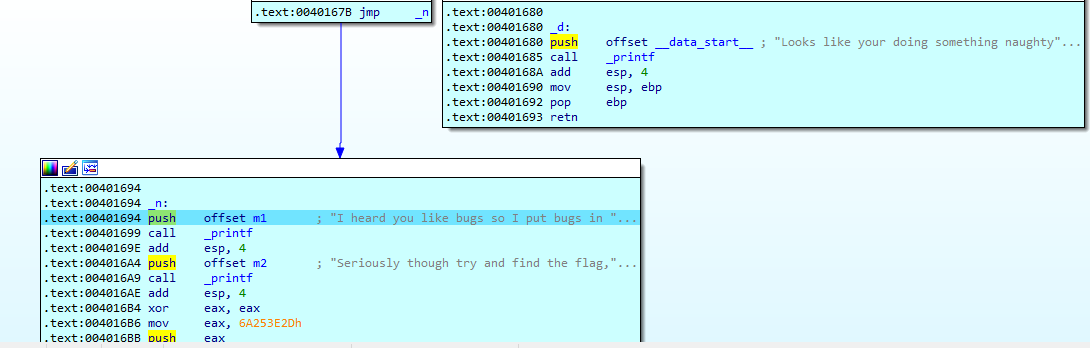
The flag is not printed so you have to grab them at return.
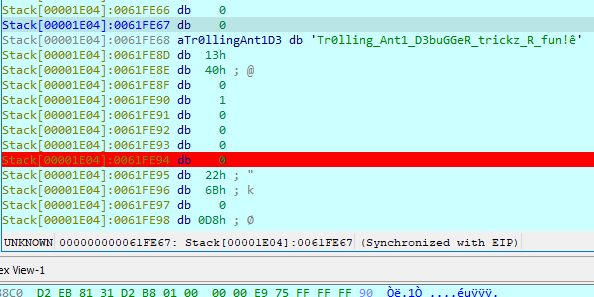
HTB{Tr0lling_Ant1_D3buGGeR_trickz_R_fun!}
Comments