Hack the Box rev Partial Encryption
Description
Static-Analysis on this program didn’t reveal much. There must be a better way to approach this…
The challenge uses a function to set execute permissions to different parts of the code as well as .
The execution chain is happening like this:
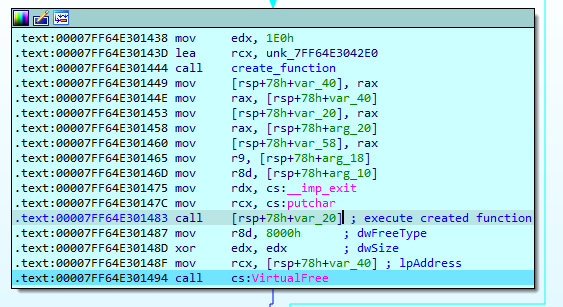
The function that prepares functions takes 2 arguments
rcx which gets an address and rdx which gets a size
There is then a loop which calls a decryption function for blocks of code :
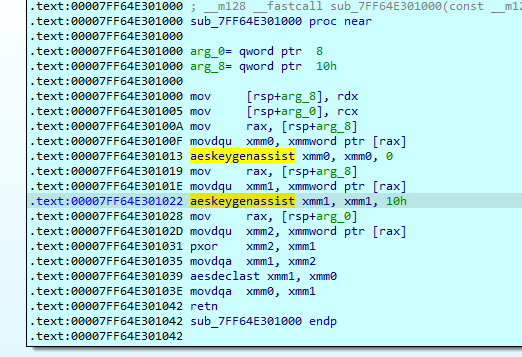
Afterwards execute permissions are set and the function is called.
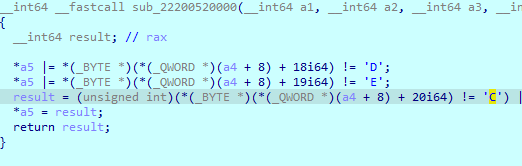
The important comparisons are
the flag should be >0x16 it should have HTB{
and then the following decrypted functions:
1.
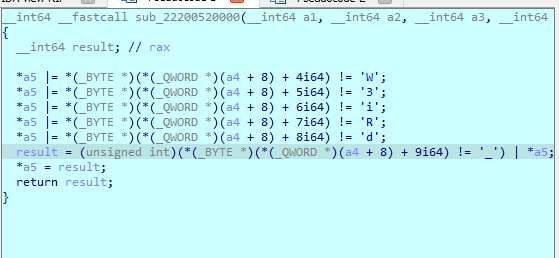 2.
2.
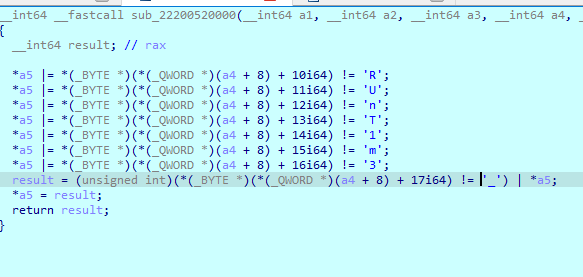 3.
3.
Give us the flag:
HTB{W3iRd_RUnT1m3_DEC}
Comments