Hack the Box rev Behind the Scenes
Behind the Scenes
Very Easy
After struggling to secure our secret strings for a long time, we finally figured out the solution to our problem: Make decompilation harder. It should now be impossible to figure out how our programs work!
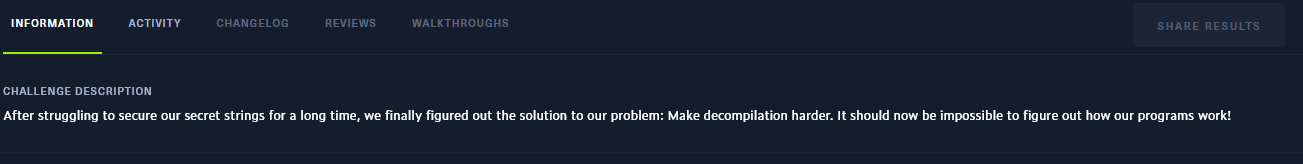
The first thing we see when opening the file with a dissasembler is the signal activity in the main function:
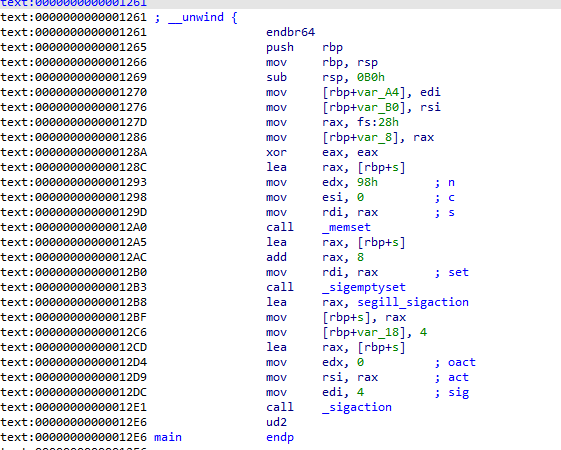
Then looking further into what the ud2 assembly instruction does we get the following:
UD2–Undefined Instruction
Generates an invalid opcode. This instruction is provided for software testing to explicitly generate an invalid opcode.
So it will trigger an exception when executed.
Further let’s see what the signal is that is handled (4) the page i found is (https://www.javatpoint.com/linux-signals) and the entry said:
- SIGILL It is an Illegal instruction. There is some machine code that is contained in the program, and the CPU cannot understand this code.
When debugging the executable when the error is met it simply jumps to the next opcodes (+2) as per the handling function:
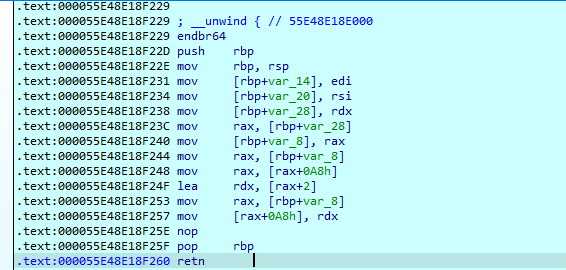
Next we follow the execution chain without needing to debug in order to understand the program.
- It checks for 2 arguments (1 by default and 2nd given by us ).
- It checks the keyword argument length (0xC= 12 characters)
- compares the first part with Itz
- compares afterwards with _0n
- compares afterwards with Ly_
- compares with UD2
Itz_0nLy_UD2
Passing the phrase gives us the flag HTB{Itz_0nLy_UD2}
Comments