UNIBUC_RE_lab_1_task01_windows
The purpose is finding interesting stuff about a binary.
The binary is not that obfuscated it uses xor to decrypt hardcoded strings.
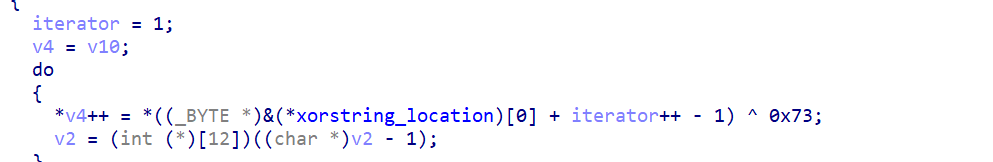 Another one can be seen here:
Another one can be seen here:
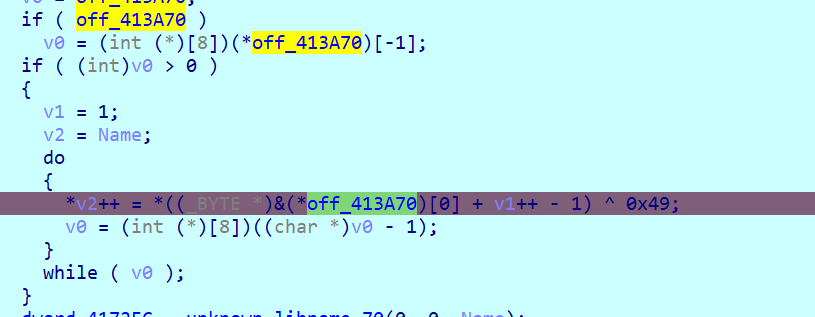 By manually reversing the process we get:
By manually reversing the process we get:
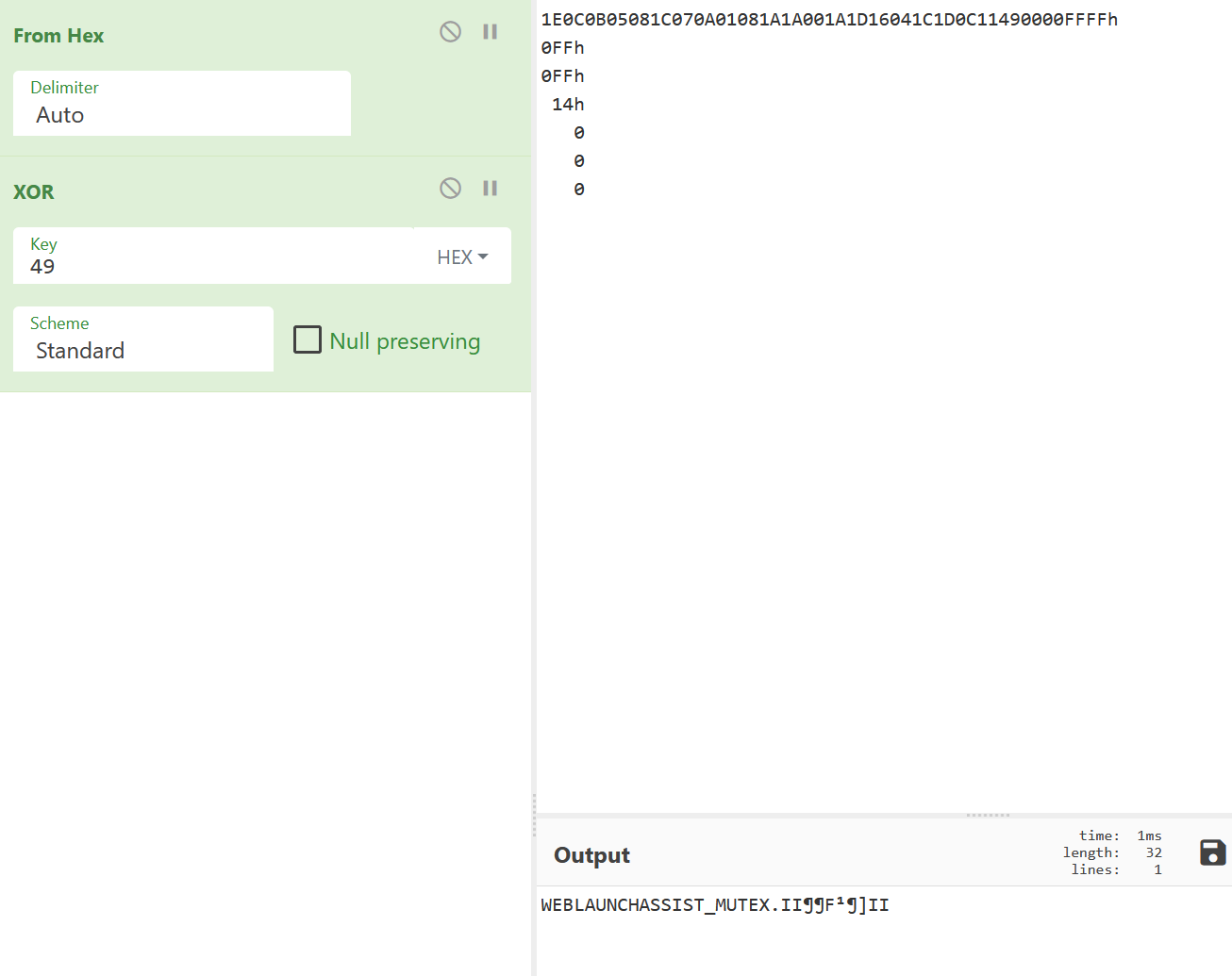 Then the process calls create_mutex_a api so this part of the malware creates a mutex with the decoded name.
Then the process calls create_mutex_a api so this part of the malware creates a mutex with the decoded name.
Next the malware wants to create a file using these strings:
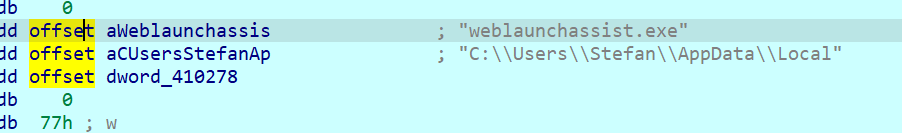
The next decryptions are related to the registry:
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
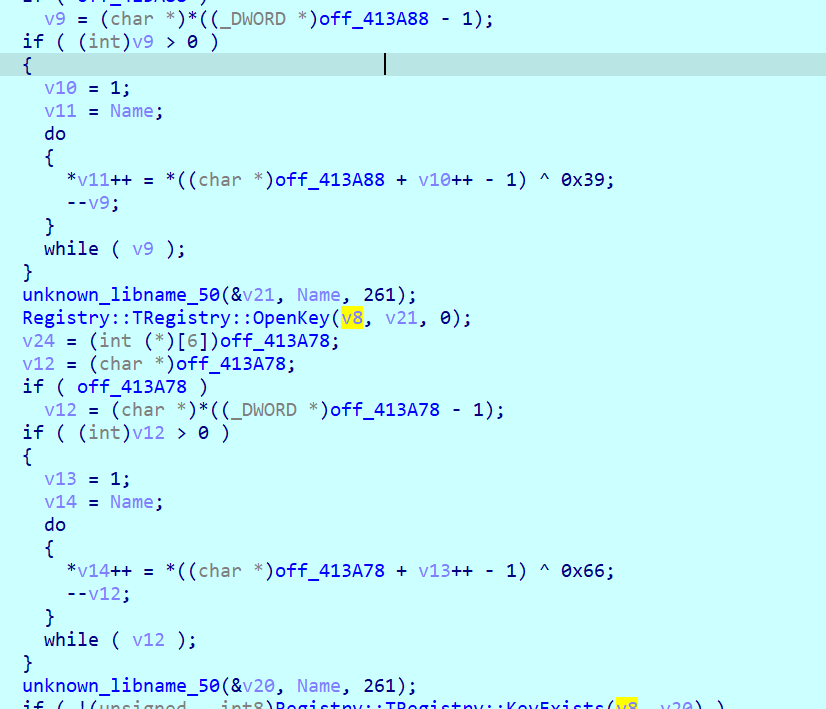 It sets the key WebLaunchAssist as a persistance mechanism
It sets the key WebLaunchAssist as a persistance mechanism
Furthermore it reads: Software\Classes\http\shell\open\command
Then it tries to connect to http://maybe.suspicious.to/secondstag using a get request.
Using OSINT techniques we can see this is part of flare on challenge 12 (https://armerj.github.io/Flare-on-Challenge-12-Part-1/)
Comments