aktiun
C binary containing python code, cannot be unzipped with any extractor medium rev.
Running the binary given to us we discover it unpacks an executable :
strace ./aktiun
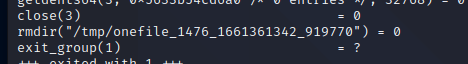
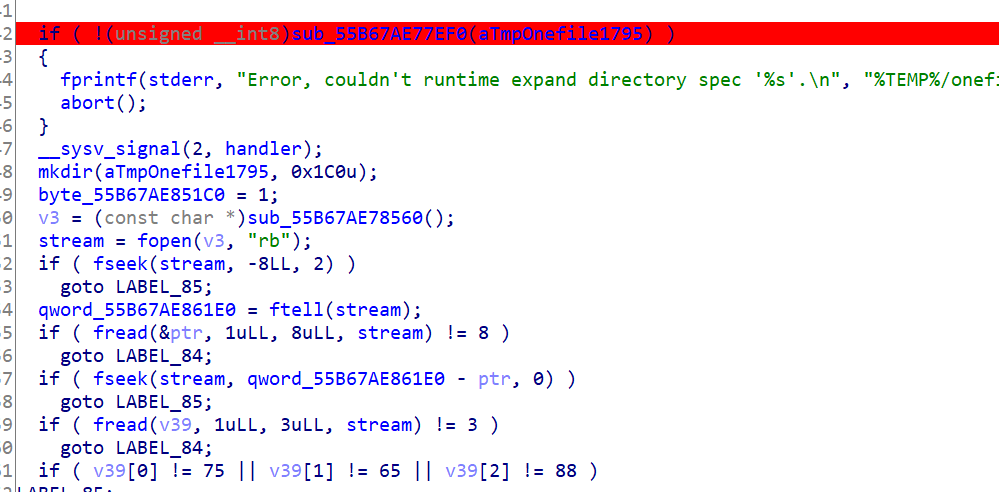
we can put a breakpoint in gdb in order to get the file or we can just put a breakpoint in ida after mkdir and all the other file making processes:
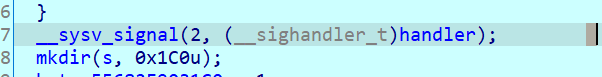
 We have to be careful to not trigger the signal call:
We have to be careful to not trigger the signal call:
We continue until there is a fork call and the folder is populated:
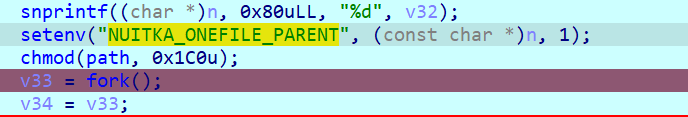
There is a binary that looks interesting to analyse in the folder named aktiun.
The binary has some interesting strings such as:
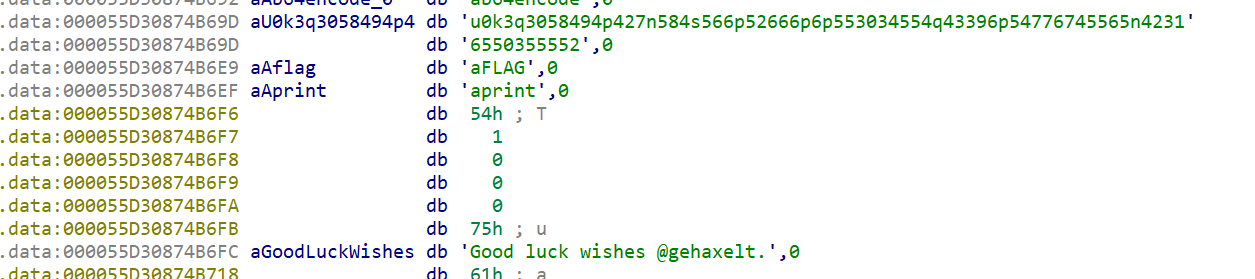
I tried (https://gist.github.com/simonw/8aa492e59265c1a021f5c5618f9e6b12) but it did not work. So i did reverse engineer the binary and found a function that basically tells me the name of the functions to be run :
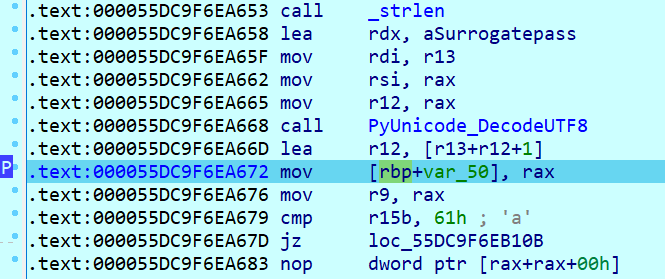 In order to filter noise i set a hardware breakpoint on the strings of interest:
In order to filter noise i set a hardware breakpoint on the strings of interest:
You can also do this by examining the modules loaded and try multiple solutions:
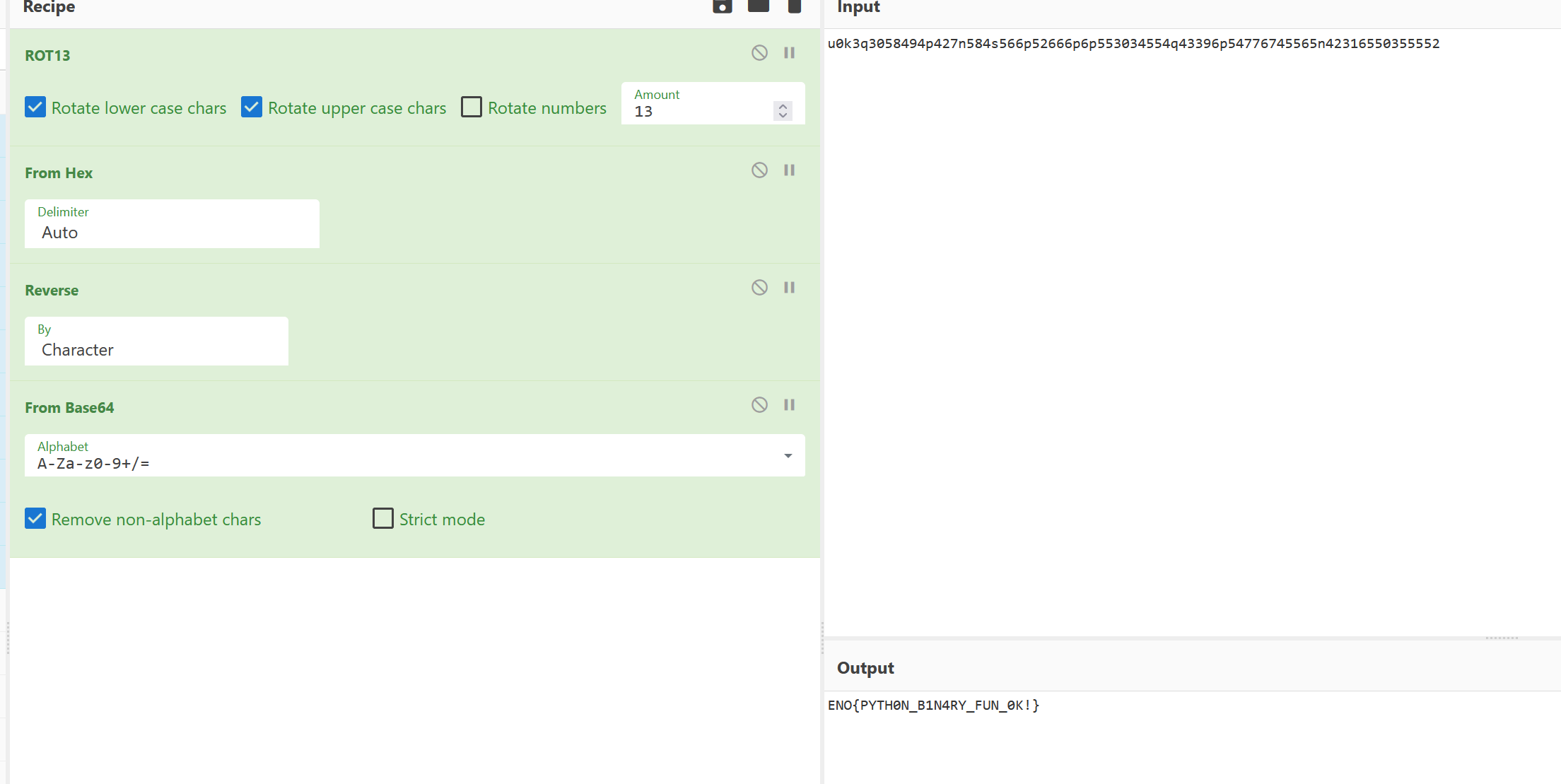
The final process is deciphering all the operations contained in the binary
Comments